Pentesting Legacy Applications with phpMyChat-Plus
One of my recent projects on education involved pentesting a legacy web application — phpMyChat-Plus. While the application itself may seem outdated, it presented an ideal opportunity to learn and apply real-world web security techniques. This article walks through the challenges I faced setting it up, the approach I took to automate the deployment, and the steps taken to discover and report critical vulnerabilities.
Deploying the Application: Challenges and Solutions
Upon starting, I quickly ran into several compatibility issues. The application, originally built in the early 2000s, failed to launch in modern environments due to outdated PHP support and broken dependency chains. This is a common problem when working with legacy software — they simply weren’t designed for the environments we use today.
Another significant blocker was the database. Although the installer interface appeared to work, it silently failed to generate critical tables for users and statistics. After some investigation (and googling a few forum threads), I found that many others encountered the same issue. I decided to write a custom SQL script to patch this, creating the missing tables manually to allow proper application functionality.
To make the setup more shareable and reproducible, I containerized the entire application using Docker. This not only solved environment-related issues but also allowed others to run the same vulnerable app with minimal effort. It turned into the foundation for a self-contained web pentesting lab, suitable for individual researchers or internal training purposes.
The app runs on a classic LAMP stack. I provided two Bash scripts:
- One to initialize the container and services,
- Another to populate the database and patch known setup bugs.
All documentation and configuration files are included in the GitHub repository.
Vulnerability Discovery and Analysis
With the app up and running, I moved into active testing using Burp Suite. Later, I cross-validated with OWASP ZAP to confirm the repeatability of the findings using open-source tools.
Burp quickly flagged numerous issues, including:
- SQL Injections (confirmed via
sqlmap) - Cross-Site Request Forgery (CSRF)
- Security Misconfigurations
- Sensitive Data Exposure
- Lack of proper session handling
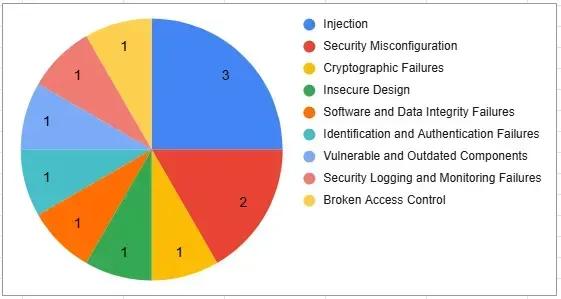
I used the OWASP Top 10 framework to classify each vulnerability. The pie chart below illustrates the distribution:
Every vulnerability was verified manually using Burp tools like Repeater and Intruder, and where needed — additional scripting to simulate full attack chains.
Reporting and Documentation
Each issue was documented with:
- Clear title and severity
- Affected endpoint or component
- Steps to reproduce
- Screenshots and payloads
- Suggested remediation
The final report can be adapted for client-facing delivery or internal use. It’s modular, so each vulnerability can be extracted into a ticket or knowledge base entry.
Lessons Learned
This project reminded me why legacy applications are still a major focus in web security. They’re often unmaintained, deployed without strong controls, and full of hidden gaps. Yet they’re also incredibly valuable as training platforms.
By the end of this project, I had:
- Built a deployable Docker lab from scratch,
- Discovered and confirmed real-world vulnerabilities,
- Automated the full setup for use by other testers,
- Improved my skills with Burp Suite, OWASP ZAP, and manual verification techniques.
The entire lab is available on GitHub here: phpmychat-lab repository
If you’re starting with pentesting or looking for a playground to sharpen your skills, this setup is a great start.
Want to try it yourself? Clone the repo, run the setup script, and start hunting. 💥
Feel free to fork and adapt it for your own lab scenarios or CTFs.